Photo credit Charles Deluvio.
We recently learned of yet another mega, corporate cybersecurity breach as Marriot reported that the personal details of 500 million guests had been stolen, including credit card details, addresses and, in some cases, passport numbers. Moreover, it looks like it ranks as one of the biggest data security breaches ever, due to the number of victims involved, and that the breach dates back to as early as 2014.
This alone is a very clear indication of how lightly the issue of cybersecurity has been taken over the years. Many executives forgot or ignored the fact there are human beings and lives behind the data. Not anymore.
What is driving cybersecurity resilience?
Building cyber resilience and mitigating the risk of cyberattack is now a top boardroom agenda item, as reputations and share prices tumble following such breaches. Yet cybersecurity breaches hitting the headlines are of course nothing new.
In 2016, a 15-year-old from Leicester hacked into the computers of the USA’s most senior spooks at the FBI and CIA, and 9,000 customers of Tesco Bank had £2.5million stolen. In May last year, the global WannaCry ransomware cyberattack hit FedEx, German rail operator Deutsche Bahn and the UK’s cherished NHS. The scale and impact of this incident really did catapult cybersecurity up the risk management agenda. And the attacks continue, as we have seen, with the Marriott group.
The cases above are the well-reported ones affecting from just a handful of individuals through to millions. Yet many more occur. The UK Department for Culture Media & Sport last year published the results of their “Cybersecurity breaches survey 2017[1]”. Of those surveyed, 46% of UK businesses had experienced cybersecurity breaches in 2017 (from a relatively small sample survey of 1,523 participants). Kroll, the risk and investigative services company, interviewed over 500 company executives for their 2017/2018 Global Fraud Risk Report. Their findings were much higher – 86% of company executives surveyed said they had experienced a cyber incident.
The rise of cyber breaches now means resilience is not just critical, but business critical. In November this year, the Bank of England, along with the Treasury, the FCA and around 40 financial institutions, conducted a war game in response to a major cyber attack. Its purpose was to ensure all meet the minimum resilience and recovery standards.
A couple of weeks later at the International Security Expo at Olympia in London, a number of leading experts in cybersecurity spoke to packed conference rooms. Organisations and companies face increasing threats from ever more sophisticated cybercriminals and they want to know how best to improve cyber resilience.
Where are the risks?
Last month, the Institute of Risk Management (IRM) published a piece in their Enterprise Magazine stating cybersecurity is the single biggest risk for 2019, highlighting an increase in cloud-based risk, data protection and compliance. The European Confederation of Institutes of Internal Auditing (ECIAA) Annual Report ‘Risk in Focus 2019’[2] summarised its findings in this graph:
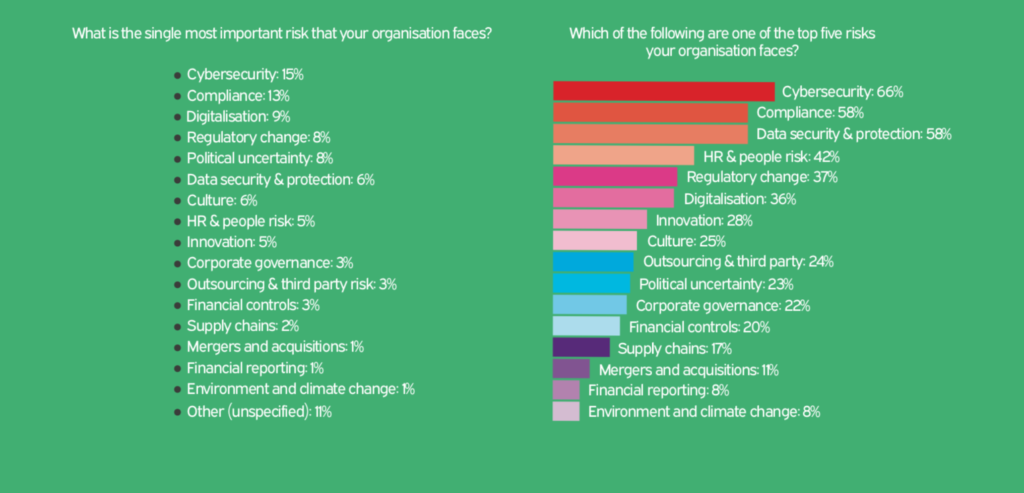
In response to this, a number of insurers and cybersecurity software firms and advisors have published a raft of reports and papers highlighting the areas of risk and vulnerability where most cyberattacks take place. These include virus/worm infestation, email phishing attacks, data breaches and ransomware.
The advent of 5G and the rise in agile and home working are also having an impact on risk, as networks can become inadvertently exposed to unsecure networks. Many also cite the reputation costs of all incidents:
ECIAA :
“The risks associated with brand and reputational harm have become more prominent as high-profile mistakes continue to be made in the public forum. Companies must think carefully about how they present themselves.”
Kroll:
“In addition to reporting extremely high incidence levels, survey respondents indicated that the repercussions were both costly and wide-ranging – negatively impacting employees, customers, reputation, relationships with regulators, and revenue. “
Managing the reputation risks – and trust
Reputation and trust is an area of risk that is extremely complex to mitigate as it is based on human reaction, and therefore, by nature, subjective. Reputation can be built, damaged and lost contingent on a number of factors. The common thread is how an individual or organisation communicates with those impacted, and what they say. This will set the tone, establish levels of trust and lay the foundations for the outcomes. Get it right, and reputation can be significantly enhanced and trust can be reinforced.
With cybersecurity, breaches and crimes, understanding the human reaction to what has happened is key. This is relevant for both individuals and organisations alike and all are victims. Unlike a physical crime, a cybercrime is virtual in nature but, as with a physical crime, victims are still victims. And aside from the top experts in the field, victims can’t see it coming. Worse still, they may be oblivious to being a victim until afterwards.
I may not have been impacted by a cybersecurity breach (to my knowledge at least) but I do have a friend who was victim to the British Airways (BA) cybersecurity breach. This August, hackers managed to get in to the BA systems and steal names, email addresses and credit card information from approximately 380,000 transactions. In the case of my BA-hacked friend, a loyal and lucrative business customer, she received a number of bland, confusing, scripted emails saying ‘problem found’, ‘problem solved’, ‘change password’, ‘contact bank’, then ‘problem not quite solved’, ‘problem solved’, ‘change password’ and ‘contact bank’ again. Like so many, she felt angry and annoyed that BA had shifted responsibility to manage the impact of their mistake. What was missing was any acknowledgement of the impact on her, her time and her wellbeing.
Since the attack, my friend has fallen victim to attempted fraudulent Uber account set-ups, phishing and suspicious calls. As she surmised “What’s next?” Her trust in BA has now gone, although she also attributes this to a culmination of other failures and an erosion of customer service in general.
Getting crisis communications right during and after a cyberattack is more than passing on information and required actions by those impacted - although this is clearly important. We are all human, and the theft of such personal data through a fibre optic cable is no different to someone dipping into a bag and stealing a passport or credit card. It is simply a different method. Those impacted are still victims of a crime.
Due to the scale and layers between the criminal, the organisation breached and the victims, what we see post-breach are perfunctory, practical announcements on what to do to minimise the potential for future criminal activity with the breached data. The human element towards respecting customer’s personal information and customer communications is absent.
The consequential cost has been customer trust, loyalty and future business. Sadly this is finally being taken seriously as this loss of trust is impacting revenues and share value. Now is the time to learn from cyber breaches, get ahead of the keyboard criminals, win back trust and strike the right tone with crisis communications.
References
[1]Cybersecurity breaches survey 2017, Department for Culture Media & Sport
[2]The European Confederation of Institutes of Internal Auditing’s annual report: Risk in Focus 2019’

